Anyone who knows me well has seen how hard we’ve been pressing the importance of security and trust in a global services delivery environment, since we founded HfS.
In short, we’re moving into a world where reactive fixes to security breaches is a sure-fire recipe for disaster. Savvy enterprises simply have to deploy proactive, holistic management practices of their data flows across systems, people and processes. What’s more, with all these new investments going into digital technology, SaaS platforms, global outsourcing initiatives and automation bots, the risks out there with our data flying all around the place – and the trust in people needed to manage these risks – is second to none.
So who better than an analyst legend of the networking and computing boom era, the founder of analyst firm Current Analysis himself, and now a year-long member of the HfS team, Fred McClimans, to have a serious deep dive into what we are calling… Trust-as-a-Service:
So Fred, why a Blueprint on security, or perhaps the better question, why trust as a Blueprint topic?
The transformation from an analog to a digital economy has been profound, giving rise to a whole new wave of business and economic models that place the consumer first and corporate assets online. This is a huge shift from the legacy models where brands controlled the message, consumers ate what was available, and managing risk meant not much more than a solid business plan, a line of credit, and Master locks on the front and back doors. That game ended a long time ago.
With most, if not all, corporate data now available online, and a massive consumer-driven omnichannel engagement model, we’ve literally given competitors and “evil-doers” a map of where to find corporate treasure, while replacing those locked doors with free keys that we hand out to every customer. While the legacy threat had to get close to inflict damage, the threat today can manifest itself from anywhere.
We’ve also seen a huge shift in the value that brands deliver to their consumers. It used to be all about the product, but now it’s increasingly about the experience – an experience that is inherently digital, less personal, and perhaps a bit more fragile. No matter how you look at it, enterprises today face risk both to their internal assets as well as to their greatest asset, their customers. Hacks and data theft – especially personal consumer data – ruin that customer experience, and decrease the level of trust. If your online or digital brand isn’t trusted by the consumer, they’ll easily go elsewhere. So, as we looked at the market for managed security services, it became clear pretty early on that it wasn’t just security, or cybersecurity, that mattered, but the trust it enabled between a brand and its customers, partners, and even employees. That realization shifted how we approached the security market. Security isn’t about securing assets, it’s about creating trusted assets that can be leveraged in the market, hence Trust-as-a-Service for our Blueprint theme.
That’s quite a shift from the traditional approach of measuring security in terms of firewalls, identity and access management, and malware detection. What was the approach you took to measure the ability to provide trust as a service? And can you share some of the key takeaways from your research?
Well, first off, this Blueprint definitely takes all the traditional security elements into account – what we refer to as the technology side of security. Security Event and Information Management (SIEM), Data Loss Prevention (DLP), Identity Access Management (IAM), app and device security are just as important today as they were a year ago, perhaps even more important as the sophistication of cyberthreats has increased. But the real area where we are seeing new value in security is in behavior, and not just user behavior, but enterprise behavior.
An increasing number of security breaches can be directly tied to enterprise behavior and processes that haven’t kept up with the growing threat. We see insider threats all the time, even though most security is directed outward. And increasingly, data isn’t just being stolen from within the enterprise, but from enterprise partners and consumers. So there’s real need to start looking at some of the business structures and processes, the deals we make, and the types of information and access we’re willing to share, that often lead to increased risk that even the best technology is unable to protect from the right prying eyes.
T-mobile had a significant (hack recently that came through one of their partners, Experian. And Sony’s infamous hack last year, that was linked to North Korea and the film “The Interview”, revealed that over 100 internal Sony system were simply unmonitored. Both of these hacks can be tied to behavior and process.
So what did we do? We started with the main technical criteria and then layered on top the ability of providers to take their customers to the next level of blended physical/digital and process/behavior maturity, which you’ll see referenced in the Blueprint as the HfS Digital Trust Framework (see Can Today’s Providers Deliver the Elements of Digital Trust?) and the Digital Security Maturity Model (see Transforming the Security Maturity Model).
What separates the winners in security apart from the others? Is there a particular technology or focus that gives them the edge in helping enterprises counter the cybersecurity threat?
Now you’re really getting into it. I think the best way to put it is to start with the technology. Every provider we looked at had solid technical chops. In fact, there’s a pretty good overlap with some of the partnerships that operate behind the scenes. And while each provider has a bit of their own special sauce in the mix, technically they all show very well.
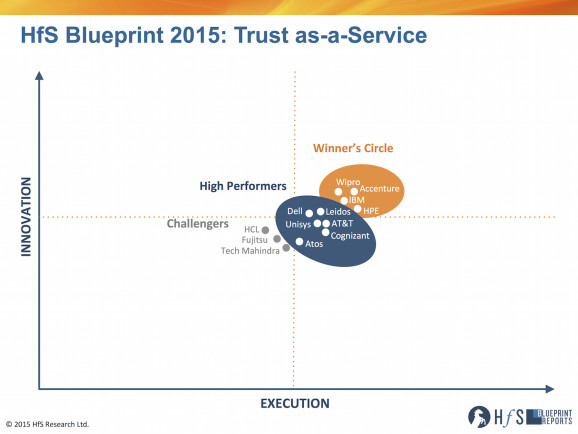
Moving up the maturity stack, what tended to set the providers apart was vision, and execution, for how enterprise security and trust enablement would materialize moving forward. Accenture and Wipro, two examples from our Winner’s Circle (along with HPE and IBM), had existing services and processes that really closely aligned with our models for Trust. Leidos and Unisys, two of our High Performers (along with Cognizant, Dell, AT&T and Atos), similarly showed a good understanding of the need to move beyond security as technology and start thinking of it as a larger enabler of corporate risk management. At the end of the day, vision, innovation, and the ability to help their clients mature digitally were all key elements of success.
You mentioned a shift from security as a way to protect assets towards security as a way to build and leverage trusted assets. Does that have a bearing on the way enterprises approach outcomes? And what recommendations do you have for them on this journey?
Phil, that mindset shift is going to play a huge part in the success, or failure, of enterprises moving forward. Security can’t afford to be an afterthought; it really needs to be thought of as a transformational enabler of a better, more trusted, business. The key recommendations? Let’s start with the basics. If enterprises aren’t aligning themselves with the Digital Trust Framework and the Security Maturity Model, they’re already behind the game. By doing this, they’ll be a bit more prepared for taking the steps needed to elevate their game.
Some specific recommendations would include elevating the responsibility for overall corporate risk and security management as close to the CEO and Board as possible; expanding their security architecture to include coordination, if not oversight, of their ecosystem partners; and a shift from a “prevent all breaches” to a “minimize breaches and control risk” approach. We’re also recommending some actions in the areas of provider relationships, in particular related to contractual flexibility, a greater level of actionable innovation, and a closer review of international privacy policies, something that delves into the role of security with regard to personal privacy and data rights.
And of course technology – automation is going to play an increasingly significant role in identifying and countering security breaches.
How about the providers? What recommendations do you have for them, and how will they need to transform themselves moving forward, or even can they?
I think transformation is going to be a challenge for some of the providers out there today. Those that are leading with tech may find themselves defining their own outcomes, and miss the opportunity to shift from service providers to service, and value, enablers. I can easily see a bifurcation of the market into two groups: one that is focused on delivering value by leveraging security as a way to create trust (as their clients go through their own digital transformation), and one that remains very tech-focused and becomes more of a modular, or on-demand, type of provider. There’s room for both, by the way.
But more directly, providers definitely need to think about security maturity in a fundamentally different fashion, which means they’ve got a lot of education to do with their clients who, based on our research, are still often thinking of security from a tech-only perspective. They also need to target the C-suite aggressively, as many of the security-related improvements and initiatives that need to be discussed go beyond the scope of a CISO.
There’s also an emerging physical/digital approach to security that winning providers will, and are starting to, adopt. Biometrics, access control systems, these are all physical systems that help provide a trusted environment, but today they’re separate from the digital security grid, unless they’ve been included as IoT devices. But the future of security services will require providers to start to leverage these devices to provide both contextual awareness of threats and help seal off threat venues.
We’re also recommending providers take a much more aggressive stance regarding corporate processes and behavior, especially from a larger risk mitigation perspective, that more emphasis be placed on aligning security services with specific business unit objectives, and that user education be significantly strengthened, to the point of bringing users in as collaborate security partners to help build a more trusted digital ecosystem.
And again, on the tech side, we’re pushing for a greater level of modularity and adaptability to keep pace with the rapid evolution of malware, spear-phishing, and embedded code hacks. This is not an easy market to be in, and they’ve got their work cut out for them.
What can we expect out of the industry in the coming year or so – it sounds like the threats show no sign of abating any time soon?
Let’s face it, the security market may never achieve a stable, or inherently safe, status. One of the constants throughout the past decade – really since the inception of digital technology – is that the level of threat always seems to meet or beat the level of protection.
Enterprises are constrained by time, technology, and budget. Hackers, especially those that are organized or sponsored, live by a different set of rules. There’s somewhat of an asymmetrical challenge at play. If you want to keep an asset 100% safe, you have to win every battle 100% of the time. But if you want to steal something, you only have to win once.
This imbalance is likely to become more pronounced as hackers find, and exploit, an increasing number of zero day vulnerabilities, especially in older, legacy systems, or as they start to leverage more of the accumulated personal data, that’s available in the dark corners of the web, to put together sophisticated personalized hacks that continue to blur the lines between the physical and digital worlds.
We’re also expecting an increase in the number of “mass risk” attacks – hacks that have the ability to cause fairly significant damage to a very large number of people, as well as an increase in smart hacks that find value in the accumulation of smaller pieces of less valued, or protected, information.
Fred McClimans can be tweeted at @fredmcclimans
HfS readers can click here to view highlights of all our 26 HfS Blueprint reports.
HfS subscribers click here to access the new HfS Blueprint Report: Trust-as-a-Service 2015
Posted in : Business Process Outsourcing (BPO), Cloud Computing, Digital Transformation, Financial Services Sourcing Strategies, Global Business Services, HfS Blueprint Results, HfSResearch.com Homepage, IT Outsourcing / IT Services, kpo-analytics, Mobility, Procurement and Supply Chain, Robotic Process Automation, SaaS, PaaS, IaaS and BPaaS, Security and Risk, smac-and-big-data, sourcing-change, The As-a-Service Economy







Appreciate the effort in evaluating these providers in this arena. There are some tier 1 vendors I don’t see listed, CGI, Infosys, Tata, eg is that because they didn’t participate or they did not satisfy some foundational criteria and therefore could not be assessed in full? Just curious – thanks
Craig: Thanks for the question. There is no “opt out” in the Blueprint process – we cover those that we feel are core to the market. In this Blueprint, we moved a bit beyond the traditional “technical” MSS approach to focus on an emerging group of providers who view security as an enabler of trust (“Security as a way to protect assets” vs “Security as a way to better leverage/utilize assets to drive enterprise outcomes”). This shift requires a stronger emphasis on valuing the behavioral aspects of security and risk within an enterprise or provider, with the understanding that core cybersecurity technologies are generally becoming commodities. Our selection criteria was geared towards this emerging market as we attempted to identify and include providers that we felt had already begun this shift in a demonstrable way. That said, this is a fast-moving market with providers across the spectrum beginning to recognize the value of this approach (this is not, btw, just a matter of “embedding security into the digital process”).
Moving into 2016, we see four different groups emerging within the broader security market, with each providing a unique value proposition and/or focus:
Group One: Traditional Security Providers, focused on technology and execution to protect the perimeter and assets of an enterprise. This is the maturing legacy market, that we expect to decline.
Group Two: Trust Providers, focused on the outcome of security services (technology plus behavior plus management maturity within the enterprise). This is the growth market, where we expect to see many traditional security providers shifting towards during the coming 12 months, potentially doubling the size of our next Trust Blueprint in 2016).
Group Three: Technology Providers, offering “tech as a service” (firewalls, malware detection, IAM, etc. increasingly bundled into primarily SMB-targeted services).
Group Four: SaaS and Platform providers, who are integrating many traditional security services into their platform offerings (e.g. SaaS, Cloud, Mobile/Comms, etc.). This group, the focus of our next Security Blueprint scheduled for release in the Spring of 2016 (“Security-as-a-Platform”), will place some competitive stress on the traditional security providers (and potentially the Trust providers) as they embed security features within their core systems and bring security one step closer to the end-to-end user experience.
If you have additional questions, please reach out to me directly – I’d welcome the opportunity to talk one on one.
Read your article with great interest. Working in the HR space and the fundamental need to handle confidential information it would be a great add-on to see how major HCM SaaS and payroll services stack up against these criteria. – thanks
AJ: I’m glad you enjoyed the post & Blurprint. I’m with you on the mapping of the Trust metrics (including some elements from the Digital Trust Framework & Security Maturity Model) to the SaaS sector – this will be touched upon as part of our next Trust/Security Blueprint: Security-as-a-Platform. Plenty of providers across the Marketing, Supply Chain, HR & Financial sectors to make it interesting!
[…] problem, McClimans explains in a recent post, is enterprises “are still often thinking of security from a tech-only […]
[…] problem, McClimans explains in a recent post, is enterprises “are still often thinking of security from a tech-only […]
[…] problem, McClimans explains in a new post, is enterprises “are still mostly meditative of confidence from a tech-only […]